Social Engineering Lab
Part-1: Attacks mapping
The goal of this part (1) is to analyse various social engineering scenarios, identify the type of attack employed, and propose effective mitigation strategies. You will work through the provided scenarios, thinking critically about how the attacks occurred and what vulnerabilities were exploited.
Scenarios
Scenario 1
An employee at a retail company, ShopTech Solutions, receives an email that appears to come from the company’s IT department. The email has the subject line: “Urgent: Password Expiration Notice.” The message claims that their password will expire in 24 hours and provides a link to "reset" it.
The employee clicks the link, which directs them to a login page that looks identical to the company’s official portal. Believing it to be legitimate, the employee enters their username and password.
Two days later, the employee notices unusual activity in their email account, such as unread messages being marked as read. Additionally, IT alerts the company that several employees have reported receiving phishing emails sent from the compromised account. The attacker also accessed internal documents shared via email, potentially exposing sensitive business information.
Scenario 2
In a busy morning at FinancePro Ltd, a junior accountant receives a phone call from someone claiming to be a representative from the company’s bank. The caller identifies themselves as "David from SecureBank" and provides details like the company’s account number to gain credibility.
"David" explains that the bank has detected suspicious transactions and urgently needs to verify recent account activities. The junior accountant, flustered by the caller's tone of authority and urgency, provides their login credentials to "help resolve the issue quickly."
Later that day, the company discovers unauthorised transactions totalling £25,000. Upon investigation, the finance department realises the credentials were used to log into the bank account and initiate the fraudulent transfers.
Scenario 3
During a routine office cleanup at DataVault Analytics, employees discover several USB drives labelled "Confidential Budget Plans 2024" scattered on desks and in the break room. Curious about the contents, an employee plugs one of the drives into their workstation and opens a file named "Budget_Details_2024.xlsx."
Unbeknownst to the employee, the file contains a hidden script that executes malware when opened. The malware silently establishes a backdoor on the workstation, providing the attacker with remote access to the company’s network. Over the next week, the attacker begins exfiltrating sensitive client data and installing additional malware to expand their access.
Scenario 4
At the headquarters of SecureNet Ltd, employees use access cards to enter the building through a secure turnstile. One afternoon, an attacker, dressed in a professional outfit and carrying a briefcase, waits outside the entrance. When an authorised employee swipes their card and enters, the attacker follows closely behind, pretending to be in a hurry and saying, "I forgot my card, can you hold the door?"
Once inside, the attacker walks around confidently, blending in with employees. They find an unlocked office and gain access to a workstation that’s logged in. On the desk, they find printouts of internal project plans and client contracts, which they photograph before leaving unnoticed. The documents contain sensitive details about an upcoming product launch.
Activities
Instructions:
- Read Each Scenario: Carefully analyse the details provided for each situation.
- Identify the Type of Attack: Based on the scenario, determine the type of social engineering attack being described.
- Explain How It Happened: Describe the steps taken by the attacker and how they successfully exploited the victim.
- Identify the Vulnerabilities: Pinpoint the weaknesses or behaviours that the attacker took advantage of.
- Propose Mitigations: Suggest at least two practical strategies to prevent similar attacks in the future.
Table Template:
Complete the following table (please download from here) for each scenario:
| Scenario | Type of Attack | How It Happened | Exploited Vulnerability | Mitigation |
|---|---|---|---|---|
| Scenario 1 | ||||
| Scenario 2 | ||||
| Scenario 3 | ||||
| Scenario 4 |
Click to view a possible answer
| Scenario | Type of Attack | How It Happened | Exploited Vulnerability | Mitigation |
|---|---|---|---|---|
| Scenario 1 | Phishing | The attacker sent an email pretending to be the IT department, including a fraudulent link to a fake login page resembling the company portal. The employee entered their credentials, which were captured by the attacker. | Lack of verification of the sender’s identity; unawareness of phishing tactics; lack of multi-factor authentication (MFA). | 1. Implement MFA to prevent unauthorised access even if credentials are compromised. 2. Conduct regular phishing awareness training to help employees recognise and avoid such attacks. |
| Scenario 2 | Vishing (Voice Phishing) | The attacker impersonated a bank representative and used urgent and authoritative language to persuade the junior accountant to disclose login credentials. | Social engineering tactics leveraging authority and urgency; lack of verification of the caller’s identity. | 1. Establish and communicate a policy never to share credentials over the phone. 2. Train employees to verify the identity of callers by directly contacting the organisation’s official channels. |
| Scenario 3 | Baiting | The attacker left USB drives labelled with enticing information in easily accessible areas. An employee, driven by curiosity, plugged in a drive and opened a file that executed malware. | Curiosity and lack of awareness about the dangers of unknown devices; no endpoint security to block malicious files. | 1. Implement endpoint security solutions to detect and block malicious scripts. 2. Educate employees about the risks of using unknown USB drives and enforce a policy against unauthorised devices. |
| Scenario 4 | Tailgating | The attacker followed an authorised employee into a secure building by pretending to have forgotten their access card. Once inside, they accessed sensitive information by exploiting an unattended, unlocked workstation. | Lack of strict physical security protocols; unauthorised individuals not challenged when entering secure areas. | 1. Introduce stricter access controls, such as turnstile logging and two-factor authentication for building entry. 2. Train employees to challenge or report unauthorised individuals attempting to follow them into secure areas. |
Part-2: Exploring the Social Engineering Toolkit (SET)
What is SET?
The Social Engineering Toolkit (SET) is an open-source framework designed for penetration testing, with a focus on social engineering. It automates tasks like phishing, credential harvesting, and malicious payload creation, enabling cybersecurity professionals to understand and mitigate social engineering threats.
Start the VM:
- Launch the admin (csf_vm1) VM from your weekly lab (
week-11). - Log in using:
- Username: csf_vm1
- Password: kalivm1
Launching SET
-
Open a terminal on your Linux machine.
-
Start SET with:
sudo setoolkit -
Accept the terms of use when prompted by typing ‘y’ to accept the agreement..
If you're using your own machine, please installed the package as follows:
sudo apt install set -y
Navigation Commands
-
Help Menu:
At any point, typehelpto display available commands. -
Exit Current Menu:
Typebackto return to the previous menu. -
Quit SET:
Typeexitto close SET.
SET Main Menu
Once SET launches, you'll see the main menu, which includes the following options:
-
Social Engineering Attacks:
- Simulates attacks such as phishing, credential harvesting, and malicious email campaigns.
-
Penetration Testing (Information Gathering):
- Gathers information about targets to aid in crafting tailored attacks.
-
Third-Party Modules:
- Allows integration with additional tools and custom scripts.
-
Update the Social-Engineer Toolkit:
- Ensures the tool is up to date (not needed for offline use).
-
Help, Credits, and Exit:
- Provides assistance and exits the tool.
Exploring Key Features
Type 1 or the number of feature to reveal more information in the terminal about the availble attack vectors
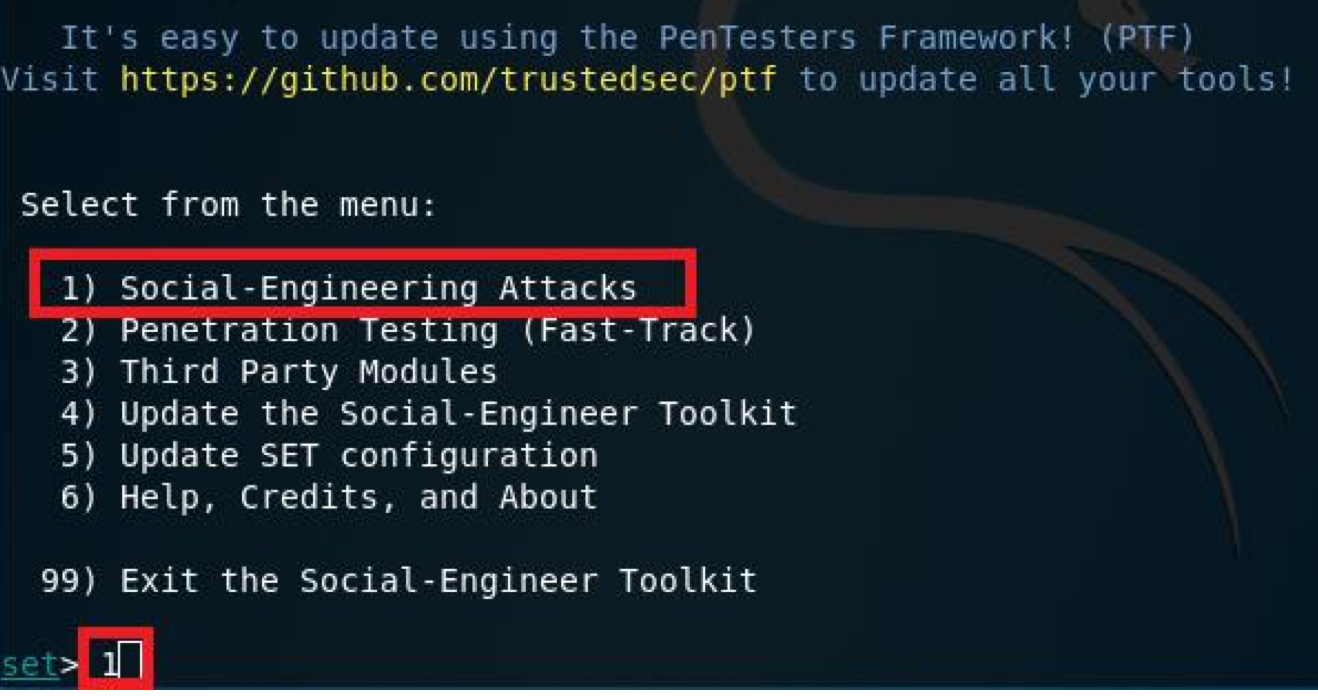
You will get something like the following:
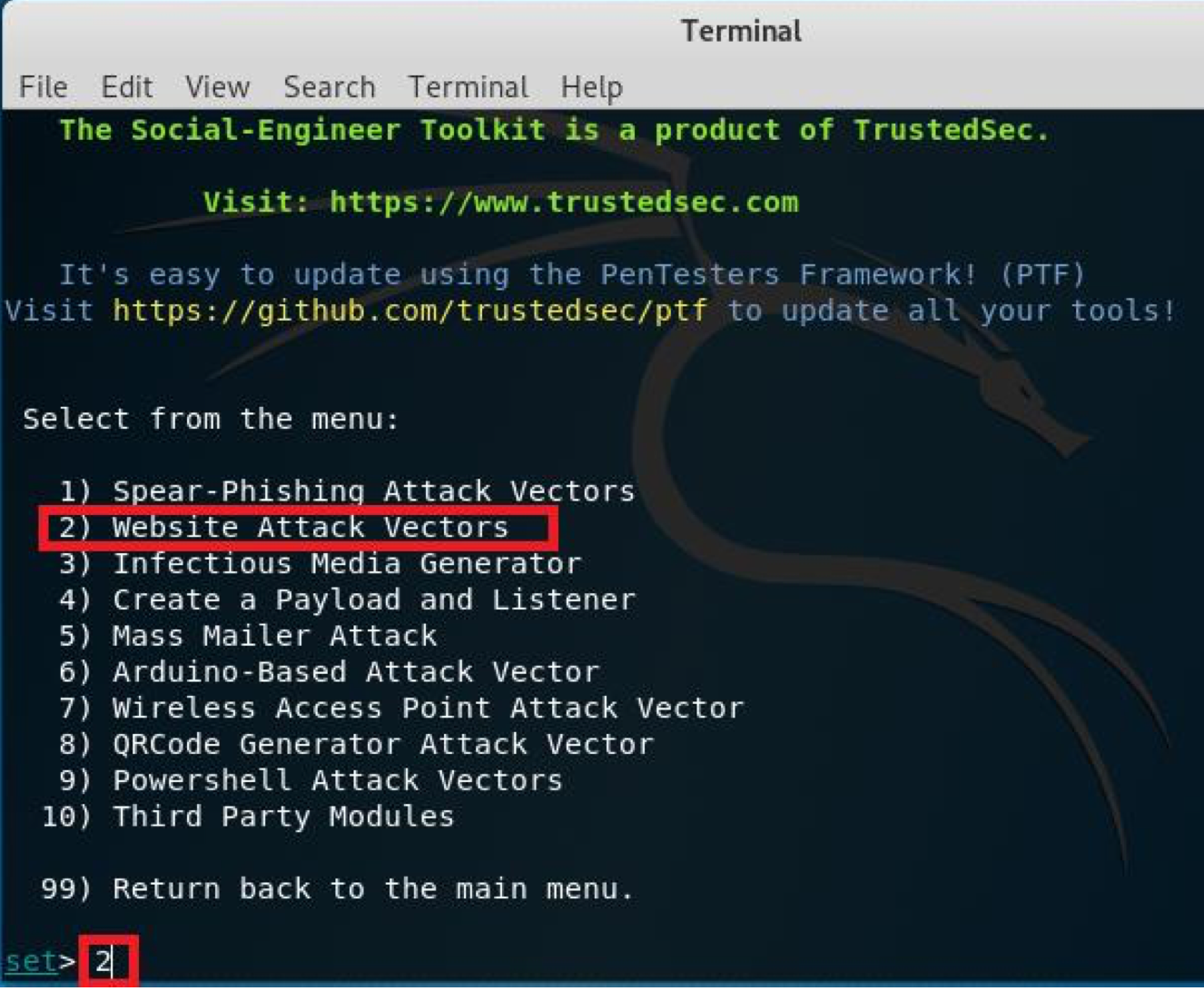
Then you can also choise from the sub-menu, e.g. if you press 2, you will get modules related to Website Attacks vectors, and so on and so forth.
Task-1: Using the Credential Harvester Method (Online and Offline)
Learn how to set up a credential harvester for phishing simulations in both online and offline environments.
1. Launch SET
- Open a terminal on your Linux machine.
- Start SET with:
sudo setoolkit
2. Navigate to the Credential Harvester Method
- From the SET main menu, select Social Engineering Attacks:
- Type the number corresponding to this option (usually
1) and press Enter.
- Type the number corresponding to this option (usually
- Select Website Attack Vectors:
- Type the number for Website Attack Vectors (usually
2).
- Type the number for Website Attack Vectors (usually
- Choose Credential Harvester Attack Method:
- Type the number corresponding to this option (usually
3) and press Enter.
- Type the number corresponding to this option (usually
3. Configure the Attack (Choose Online or Offline)
Option A: Online Setup (Only if you're using your own machine)
- Choose the Cloning Option:
- Select the Site Cloner option by typing its number (usually
2) and pressing Enter.
- Select the Site Cloner option by typing its number (usually
- Enter the IP Address:
- You can find your IP address by using
ifconfigon a seprate terminal. - Input your machine’s IP address (e.g.,
aaa.bbb.ccc.dddfor localhost or your LAN IP if testing on another device).
note: replace
aaa.bbb.ccc.ddwith your IP address. - You can find your IP address by using
- Specify the Target URL:
- Enter the URL of an online website you want to clone (e.g.,
http://www.facebook.com). - SET will fetch the online website and create a clone for phishing.
- Enter the URL of an online website you want to clone (e.g.,
Option B: Offline Setup
-
Prepare Your Static HTML File:
- I have saved a static HTML file (e.g.,
facebook.html) in the directory/home/csf_vm1/, and you can do for any other.
- I have saved a static HTML file (e.g.,
-
Host the File Using Python:
-
Open a another terminal and navigate to the directory containing your file:
cd /home/csf_vm1 -
Start a lightweight HTTP server:
python3 -m http.server 8080 -
Your file will now be hosted at:
http://127.0.0.1:8080/facebook.html
-
4. Launch the Attack
- Once configured, SET will host the cloned website (online or offline) on your machine.
- Open a web browser and navigate to the IP address you specified earlier (e.g.,
aaa.bbb.ccc.dd).
note: replace
aaa.bbb.ccc.ddwith your IP address.
5. Test the Attack
- Enter dummy credentials on the hosted page to simulate a victim’s actions.
- Observe the terminal output where SET logs the captured credentials in real time.
Example Output
When credentials are entered on the fake login page, you will see output similar to this in the terminal:
[*] WE GOT A HIT! Printing the details...
[*] USERNAME: victimuser
[*] PASSWORD: victimpassword123
Viewing SET Logs and Reports
To view reports and logs generated by the Social Engineering Toolkit (SET), follow these steps.
- Ensure you are logged in as the root user or have superuser privileges.
- Use the following command to switch to root:
sudo su
Commands to View SET Reports
-
Navigate to SET Logs Directory:
- SET logs and saved files are located in the
/root/.set/directory. - Change to this directory:
cd /root/.set/
- SET logs and saved files are located in the
-
List Available Logs:
- Use the
lscommand to see all files and logs in the directory:ls
- Use the
-
View Specific Log Files:
- Navigate to
reportusingcd report, then enterlsto view all available reports. if your report name isxxxxyyyy - View
xxxxyyyy.log:cat logs/xxxxyyyy.log
- Navigate to
-
Copy Logs for Reporting:
- If you want to copy the logs to a user-accessible directory (e.g.,
~/Documents):cp logs/xxxxyyyy.log ~/Documents/
- If you want to copy the logs to a user-accessible directory (e.g.,
Notes
- Logs for specific attacks, such as credential harvesting, are often stored in subdirectories under
/root/.set/. - Ensure to maintain the confidentiality of sensitive data captured in the logs during your exercises.
Reflection
- Discussion:
- Compare the results of the online and offline setups. What are the advantages and limitations of each approach?
- How could attackers exploit these methods in real-world scenarios?
- Mitigation Strategies:
- Propose at least two defences (e.g., user awareness training, multi-factor authentication).
Extra
SET User Manual Made for SET 6.0 Prepared by: David Kennedy Hacker, TrustedSec