Part-1: Incident Report Exercises SANS
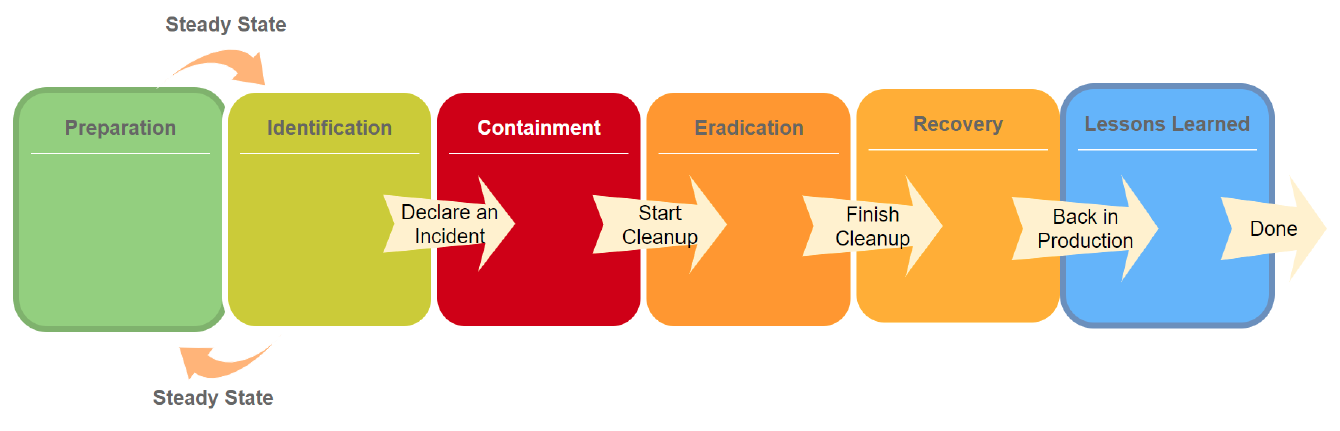
Exercise 1: Applying the SANS Six-Step Process
Scenario: Ransomware Attack on a Small Business
A small business is hit by a ransomware attack. The attackers encrypted critical business files, including customer data and financial records. A ransom demand of 2 Bitcoin was made, with a threat to leak sensitive customer information online if payment isn’t made within 48 hours.
- Key Observations:
- The ransomware entered the network through an email attachment opened by an employee in the Marketing Department.
- Critical files were encrypted, and a ransom note was displayed on several systems.
- Backups were not up to date, leaving the organisation vulnerable.
- No evidence of data exfiltration was found, but the threat of leaking data remains.
Tasks:
-
Follow the SANS Steps:
- Work through the incident using the SANS six-step process:
- Preparation:
- Identify gaps in the organisation's preparedness, such as outdated backups and phishing defences.
- Identification:
- Discuss how the ransomware was detected and its impact assessed.
- Containment:
- Propose immediate actions to isolate affected systems and prevent the ransomware from spreading.
- Eradication:
- Detail how the ransomware should be removed and vulnerabilities patched.
- Recovery:
- Suggest steps to restore files and resume normal operations (e.g., restoring from backups).
- Lessons Learned:
- Analyse the attack to identify areas of improvement, including backup policies and phishing awareness.
- Preparation:
- Work through the incident using the SANS six-step process:
-
Deliverables:
- Prepare a doc outlining:
- Actions taken at each SANS step.
- Recommendations for future incident prevention, including technology upgrades and staff training.
- Prepare a doc outlining:
Part-2: Incident Report Exercises using IR form
To carry out the following tasks, please use this form
The table below is an example of a pre-populated form.
| # | Field | Details |
|---|---|---|
| 1 | Report No.: | 00123 |
| 2 | Title of Report: | Ransomware Attack on HR Database |
| 3 | Incident Reported By: | John Smith (IT Manager) |
| 4 | Date and Time of Incident: | Date: 2024-11-27 Time: 14:35 |
| 5 | Location of Incident: | Headquarters - Server Room |
| 6 | Description of Incident: | |
| Asset(s): | HR Database Server, Backup Server | |
| Criticality: | High (Critical business operations affected) | |
| Incident: | The HR database server was encrypted by a ransomware attack, blocking access to payroll and personnel records. Initial investigation suggests the entry point was a phishing email containing a malicious link. The backup server was also targeted but remained unaffected. | |
| 7 | Incident Lead: | Jane Doe (Incident Response Team Lead) |
| 8 | Issue Status: | (1) Reported |
| IT IR Case Number: | IR-2024-001 | |
| 9 | Related Incidents: | Previous phishing attempt reported on 2024-11-25 targeting finance department employees. |
| 10 | Category: | Malicious code (Ransomware) |
| 11 | Severity: | (1) High |
| 12 | Summary of Resolution Plan: | |
| - Isolate the affected HR database server from the network to prevent further spread. | ||
| - Conduct forensic analysis to determine the origin and extent of the breach. | ||
| - Use unaffected backups to restore the HR database server. | ||
| - Apply security patches and updates to the affected systems. | ||
| - Implement email filtering solutions and conduct phishing awareness training. | ||
| 13 | Planned Resolution Date: | 2024-11-28 |
| 14 | Summary of Lessons Learned: | |
| - Multi-factor authentication should be enforced for all critical systems. | ||
| - Regular backup testing is essential to ensure recoverability. | ||
| - Enhanced email security measures are necessary to mitigate phishing risks. |
Exercise 2: Malware Infection in the HR Department
Scenario 1: Malware Outbreak
- Date and Time: 28th November 2024, 10:15.
- Incident Reported By: Jane Doe, HR Manager.
- Location of Incident: Human Resources Department.
- Description:
- Multiple systems in the HR department began operating unusually slowly.
- Upon investigation, it was discovered that a malware program was encrypting files and communicating with an external server.
- Employees received phishing emails disguised as an urgent HR policy update.
- Affected Assets:
- HR laptops and desktops (HR-PC01, HR-PC02, HR-LAP01).
- The central HR file server storing employee data.
- Criticality: High.
- Observations:
- Malware entered via a phishing email attachment.
- Encryption activity initiated after an employee opened the attachment.
- Files on shared network drives were also encrypted.
- Resolution Plan:
- Disconnect all affected systems from the network immediately.
- Conduct a full scan of all HR department systems to identify the malware.
- Restore encrypted files from the last known good backup.
- Notify affected employees and the IT department.
- Educate employees on recognising phishing emails.
- Enhance email filtering systems and deploy endpoint detection tools.
Task 1:
-
Fill Out the Incident Report Form:
- Use the scenario details to document the incident.
- Key areas to document include the description of the incident, affected assets, severity, and criticality.
-
Propose a Mitigation Plan:
- Outline steps to improve the organisation's phishing awareness and malware defences, including technological solutions (e.g., endpoint detection and response) and training.
-
Submit Recommendations:
- Provide suggestions on updating policies and incident response procedures to prevent future occurrences.
Below is a solutions
| # | Field | Details |
|---|---|---|
| 1 | Report No.: | 00124 |
| 2 | Title of Report: | Malware Outbreak in HR Department |
| 3 | Incident Reported By: | Jane Doe (HR Manager) |
| 4 | Date and Time of Incident: | Date: 2024-11-28 Time: 10:15 |
| 5 | Location of Incident: | Human Resources Department |
| 6 | Description of Incident: | |
| Asset(s): | HR laptops and desktops (HR-PC01, HR-PC02, HR-LAP01), central HR file server storing employee data. | |
| Criticality: | High (Critical business operations affected) | |
| Incident: | Multiple systems in the HR department experienced abnormal slowness. Investigation revealed a malware program encrypting files and communicating with an external server. The malware was introduced via phishing emails disguised as an urgent HR policy update. Files on shared network drives were also encrypted. | |
| 7 | Incident Lead: | Jane Doe (Incident Response Team Lead) |
| 8 | Issue Status: | (1) Reported |
| IT IR Case Number: | IR-2024-002 | |
| 9 | Related Incidents: | Phishing emails reported on 2024-11-25 targeting HR and Finance employees. |
| 10 | Category: | Malicious code (Malware) |
| 11 | Severity: | (1) High |
| 12 | Summary of Resolution Plan: | |
| - Disconnect all affected systems from the network to prevent further spread. | ||
| - Conduct a full malware scan across all HR department systems. | ||
| - Restore encrypted files from the last known good backup. | ||
| - Notify all affected employees and escalate to the IT department. | ||
| - Enhance email filtering systems and deploy endpoint detection tools. | ||
| - Conduct phishing awareness training for employees. | ||
| 13 | Planned Resolution Date: | 2024-11-29 |
| 14 | Summary of Lessons Learned: | |
| - Email filtering and endpoint detection are critical to reducing malware threats. | ||
| - Regular backup testing ensures effective disaster recovery. | ||
| - Awareness and training can significantly mitigate phishing risks. |
Exercise 3: Unauthorised Data Access
Scenario 2: Data Exfiltration
- Date and Time: 29th November 2024, 14:30.
- Incident Reported By: Michael Smith, IT Security Engineer.
- Location of Incident: Finance Department.
- Description:
- A suspicious transfer of sensitive financial data was flagged by the intrusion detection system (IDS).
- Logs show that a compromised employee account was used to access financial records.
- Affected Assets:
- Finance file server containing budget and revenue data.
- Compromised user account (finance_john).
- Criticality: High.
- Observations:
- Unauthorised access occurred from a remote IP address (202.45.67.89).
- Large volumes of financial data were transferred to an external server.
- Suspicious login activity was traced back to stolen employee credentials.
- Resolution Plan:
- Disable the compromised account immediately.
- Analyse access logs to determine the scope of the breach.
- Notify affected departments and legal counsel.
- Enhance authentication mechanisms (e.g., multi-factor authentication).
- Investigate the origin of the stolen credentials and implement additional security controls.
Task 2:
-
Fill Out the Incident Report Form:
- Document the incident thoroughly, including affected assets, criticality, and suspected severity.
- Categorise the type of incident (e.g., unauthorised access, potential data breach).
-
Conduct Root Cause Analysis:
- Analyse what may have led to the incident. Highlight any procedural lapses or weaknesses in the current security controls (e.g., poor identity verification during password resets).
-
Propose Corrective Actions:
- Suggest measures to prevent unauthorised access in the future. These could include technical fixes (e.g., multi-factor authentication), procedural changes (e.g., stricter helpdesk protocols), or employee training.
-
Reflect on Regulatory Implications:
- Consider what steps the organisation needs to take to comply with data privacy regulations (e.g., GDPR, CCPA) in response to this incident.
See solutions below
| # | Field | Details |
|---|---|---|
| 1 | Report No.: | 00125 |
| 2 | Title of Report: | Data Exfiltration in Finance Department |
| 3 | Incident Reported By: | Michael Smith (IT Security Engineer) |
| 4 | Date and Time of Incident: | Date: 2024-11-29 Time: 14:30 |
| 5 | Location of Incident: | Finance Department |
| 6 | Description of Incident: | |
| Asset(s): | Finance file server containing budget and revenue data, compromised user account (finance_john). | |
| Criticality: | High (Critical business operations affected) | |
| Incident: | A suspicious transfer of sensitive financial data was flagged by the intrusion detection system (IDS). Logs indicate a compromised employee account was used to access financial records. Unauthorised access originated from a remote IP address (202.45.67.89), and large volumes of financial data were transferred to an external server. The breach is attributed to stolen employee credentials. | |
| 7 | Incident Lead: | Michael Smith (Incident Response Team Lead) |
| 8 | Issue Status: | (1) Reported |
| IT IR Case Number: | IR-2024-003 | |
| 9 | Related Incidents: | No prior related incidents reported. |
| 10 | Category: | Data Exfiltration |
| 11 | Severity: | (1) High |
| 12 | Summary of Resolution Plan: | |
| - Disable the compromised account immediately. | ||
| - Analyse access logs to determine the scope of the breach. | ||
| - Notify affected departments and legal counsel. | ||
| - Enhance authentication mechanisms (e.g., multi-factor authentication). | ||
| - Investigate the origin of the stolen credentials and implement additional security controls. | ||
| 13 | Planned Resolution Date: | 2024-11-30 |
| 14 | Summary of Lessons Learned: | |
| - Multi-factor authentication is critical to preventing unauthorised access. | ||
| - Continuous monitoring of suspicious activity can help detect breaches earlier. | ||
| - Strong password policies and credential protection mechanisms are essential. |
Part-3: Red, Blue and Purple Teaming (Research-Based Team Collaboration)
Scenario: Supply Chain Security Threat
Your organisation is reviewing its security posture following recent industry reports about supply chain attacks. These attacks often occur when a trusted vendor or partner’s software is compromised, resulting in malicious updates being distributed to customers. The organisation has asked your team to research how different cybersecurity roles (Red, Blue, and Purple Teams) can address these risks and strengthen supply chain security.
Tasks:
-
Red Team Research:
- Investigate how attackers exploit supply chain vulnerabilities. Research and report on:
- Common techniques used in supply chain compromises (e.g., code injection, compromised updates).
- Real-world examples of supply chain attacks (e.g., SolarWinds, Kaseya).
- Recommendations for how organisations can simulate such attacks to identify weaknesses.
- Investigate how attackers exploit supply chain vulnerabilities. Research and report on:
-
Blue Team Research:
- Explore how to detect and mitigate supply chain attacks. Research and report on:
- Key indicators of compromise (IoCs) and monitoring strategies for malicious software updates.
- Best practices for vetting third-party vendors and securing software supply chains.
- Case studies of successful mitigations in supply chain attacks.
- Explore how to detect and mitigate supply chain attacks. Research and report on:
-
Purple Team Research:
- Examine how Red and Blue Teams can collaborate to address supply chain risks. Research and report on:
- Strategies for sharing information between teams to improve detection and prevention.
- Frameworks or standards that guide supply chain security (e.g., NIST Cybersecurity Framework, ISO 27001).
- Policies or tools organisations can adopt to enhance vendor and software security.
- Examine how Red and Blue Teams can collaborate to address supply chain risks. Research and report on:
Possible soluations
Scenario: Supply Chain Security Threat
1. Red Team
-
Common Techniques in Supply Chain Compromises:
- Code Injection: Malicious code is inserted into software updates or development pipelines, often unnoticed by the vendor.
- Compromised Updates: Threat actors infiltrate update mechanisms to deliver malicious updates to end-users.
- Dependency Hijacking: Exploiting insecure open-source libraries or dependencies used by trusted software vendors.
- Credential Theft: Gaining access to vendor systems by stealing employee credentials or exploiting weak access controls.
-
Real-World Examples:
- SolarWinds (2020): Attackers compromised SolarWinds’ Orion platform, inserting a backdoor into updates, affecting multiple high-profile organisations.
- Kaseya (2021): Exploited vulnerabilities in the VSA platform to deploy ransomware via compromised vendor software.
- CCleaner (2017): Attackers injected malicious code into legitimate software updates, affecting millions of users.
-
Recommendations for Simulating Supply Chain Attacks:
- Use penetration testing tools to mimic code injection or dependency hijacking scenarios.
- Simulate compromised update mechanisms by deploying test payloads through software pipelines.
- Assess third-party software dependencies for vulnerabilities and outdated components.
- Conduct table-top exercises focusing on supply chain attack scenarios.
2. Blue Team
-
Key Indicators of Compromise (IoCs) and Monitoring Strategies:
- IoCs:
- Unexpected changes in software behaviour post-update.
- Anomalous network traffic to external IPs or domains after a software update.
- Unauthorised access to software build or update servers.
- Monitoring Strategies:
- Implement Endpoint Detection and Response (EDR) to monitor unusual behaviours.
- Utilise threat intelligence to identify known malicious indicators related to vendors.
- Perform regular scans of software binaries to detect changes or malicious code.
- IoCs:
-
Best Practices for Vetting Vendors and Securing Supply Chains:
- Conduct thorough vendor risk assessments, including cybersecurity posture evaluations.
- Require third-party vendors to comply with industry security standards (e.g., ISO 27001, SOC 2).
- Establish secure software development practices, including code signing and secure update mechanisms.
- Monitor vendor systems and interactions for any anomalous activity.
-
Case Studies:
- Microsoft Exchange Supply Chain Attack (2021): Detected anomalous behaviour early using internal monitoring systems and partnered with external agencies to mitigate.
- Target (2013): Breach via an HVAC vendor underscored the importance of isolating third-party vendor systems and improving credential management.
3. Purple Team
-
Strategies for Collaboration Between Red and Blue Teams:
- Share Red Team findings with the Blue Team to develop proactive monitoring and mitigation strategies.
- Conduct joint exercises, where the Red Team simulates supply chain attacks and the Blue Team tests detection and response.
- Use a feedback loop for continuous improvement in attack simulation and defence techniques.
-
Frameworks or Standards:
- NIST Cybersecurity Framework:
- Focuses on identifying, protecting, detecting, responding, and recovering from supply chain threats.
- ISO 27001:
- Provides guidelines for managing third-party risks and securing the software development lifecycle.
- Supply Chain Risk Management (SCRM):
- Specific NIST guidelines for addressing supply chain risks.
- NIST Cybersecurity Framework:
-
Policies and Tools to Enhance Security:
- Policies:
- Enforce strict access controls and multi-factor authentication for vendor systems.
- Mandate periodic security audits for all third-party vendors.
- Tools:
- Software Composition Analysis (SCA) tools to detect vulnerabilities in third-party components.
- Secure DevOps (DevSecOps) practices to integrate security at every stage of the software development lifecycle.
- Threat intelligence platforms for early detection of supply chain-related threats.
- Policies: