Importance of an IR Plan
- Defines what
constitutesan "incident" for the organisation. - Provides clear, guided procedures for responding to incidents.
- Prepares organisations for Operational Technology (OT) and cybersecurity challenges.
Incident Response Processes
There are two distinct aspects to incident response:
- Incident response preparation
- Incident response handling
1. Incident response preparation:
- Occurs
periodically,withoutany identifiedincident. - Focus:
Prepareteamsto handle incidentsefficientlyandeffectively.
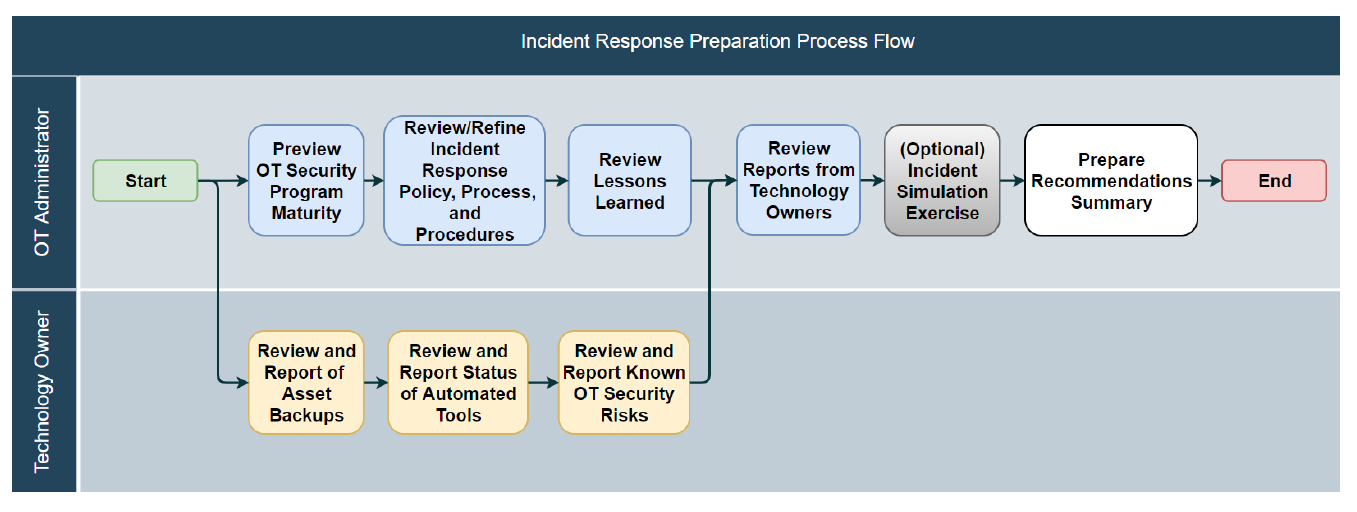
1. Incident response preparation: Cont'
- Inputs:
- OT security policies, processes, and procedures.
- Asset inventory.
- Completed incident response forms.
- Outputs:
- Updated IR policy, processes, and procedures.
- Recommendations summary document.
2. Incident Handling
-
Provide a framework for
systematicandefficientincidentresponse. -
Minimisechaosby predefining roles and responsibilities. -
Inputs:
- Blank incident response form, pre-prepared team, etc.
-
Outputs:
- Completed incident response form.
- Restored system operations.
- Communicated closed status.
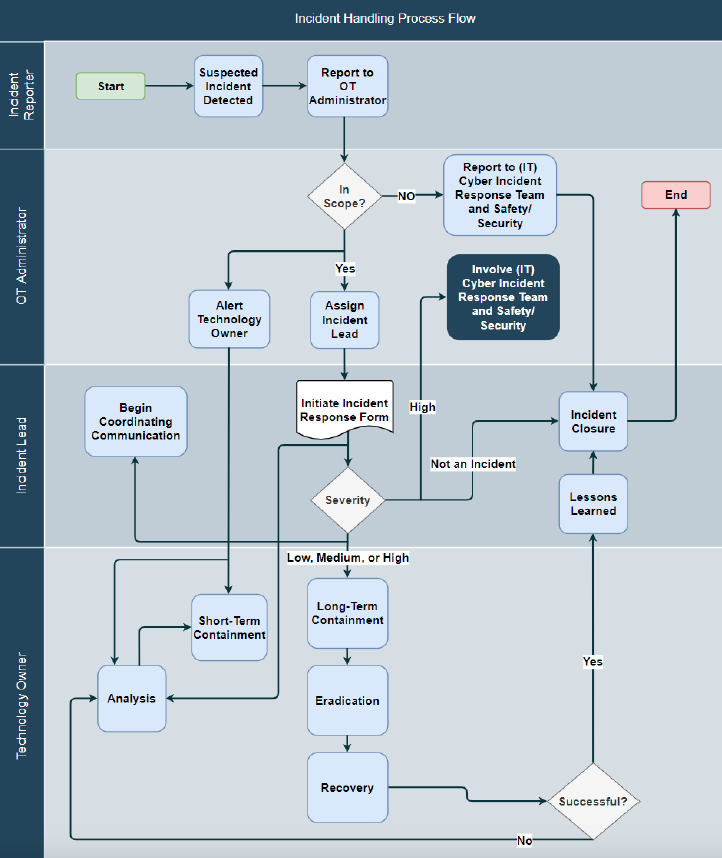
Incident response procedures: SANS
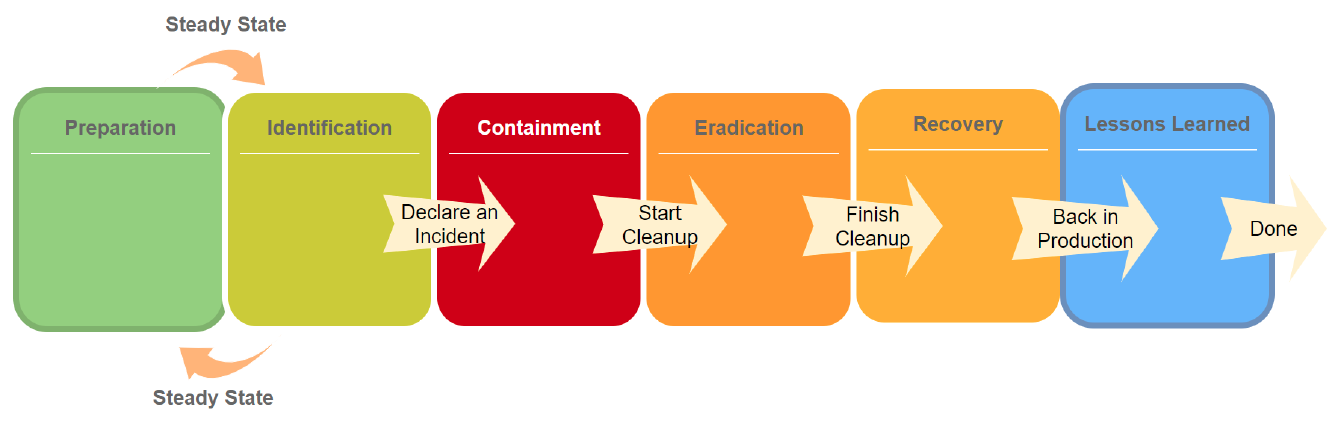
Others models:
-
-
-
ISO/IEC
SANS: Step 1 - Preparation
Objective:
- Ensure the organisation is
readytohandleincidents effectively.
Key Actions:
Developandmaintainincident responsepoliciesandprocedures.Assembleandtrainthe incident responseteam.Gathertools and resources, such as monitoring systems andforensicstools.Conductregularincident response drills.
SANS: Step 2 - Identification
Objective:
- Detect and confirm the occurrence of an incident.
Key Actions:
Monitorsystems for anomalies and suspicious activities.Analyselogs, alerts, and other data sources.Classifyincidents based on type and severity.Notifythe incident response team of confirmed incidents.
SANS: Step 3 - Containment
Objective:
Preventfurtherdamageand limit the impact of the incident.
Key Actions:
- Implement short-term
containment measures(e.g., isolating affected systems). Developlong-termcontainmentstrategiesfor ongoing incidents.- Preserve evidence for forensic analysis.
Goal:
Stabilisethe environment whilemaintainingthe integrity ofevidence.
SANS: Step 4 - Eradication
Objective:
Eliminatethecauseof the incident.
Key Actions:
Identifyand remove malware, unauthorised access, or compromised accounts.Patch vulnerabilitiesexploited during the incident.- Conduct thorough
scans(e.g., pentest)to ensure the threat has been eradicated.
SANS: Step 5 - Recovery
Objective:
- Restore systems and operations to normal.
Key Actions:
Rebuildor restore affected systems frombackups.- Verify systems are secure and
fully operational. Monitorfor lingering threats or vulnerabilities.
Goal:
- Safely return to normal business operations.
SANS: Step 6 - Lessons Learned
Objective:
Analysethe incident toimprovefutureresponses.
Key Actions:
- Conduct a
post-incident reviewwith all stakeholders. - Identify
gapsin the incidentresponseprocess. Updatepolicies,procedures, and training based on findings.
Outcome:
- Build a
more resilientincident response program.
Summary of the SANS Process
- Preparation: Get ready for incidents before they happen.
- Identification: Detect and confirm incidents quickly.
- Containment: Limit the spread of the threat.
- Eradication: Remove the root cause of the incident.
- Recovery: Return systems to normal operation.
- Lessons Learned: Improve based on the incident experience.
Incident report form
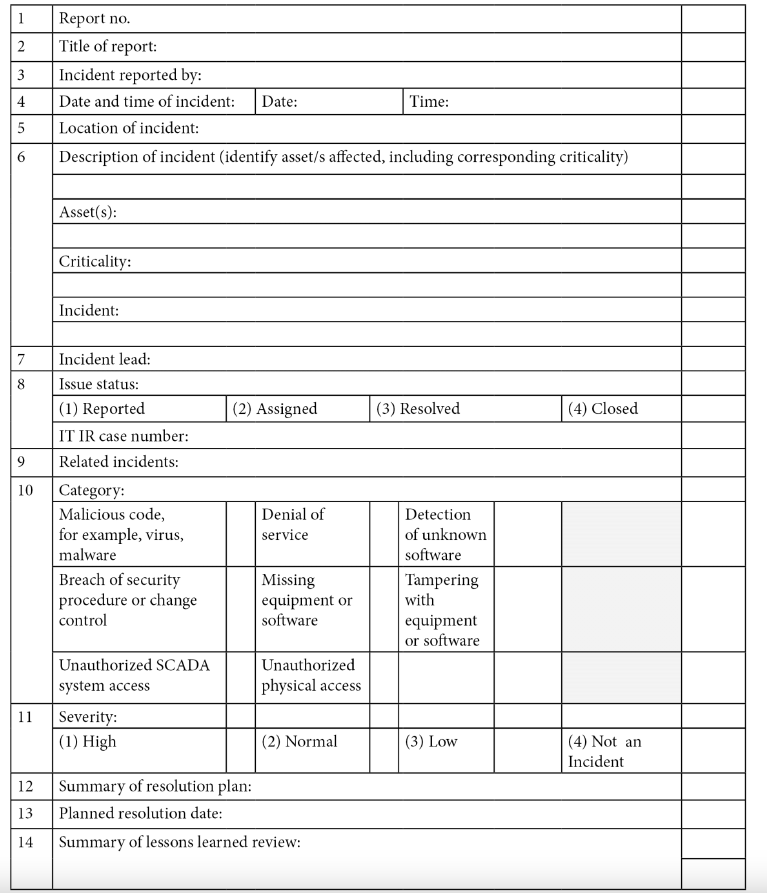
You can download from here
Red, Blue, and Purple Teaming in Incident Response
-
In cybersecurity, effective incident response requires a holistic approach that combines both
offensiveanddefensivetactics. -
Red, Blue, and Purple Teaming are essential components in testing, defending, and enhancing an organisation's security posture.

1. Red Teaming
The Red Team acts as an adversary, simulating real-world cyberattacks to identify vulnerabilities in an organisation's security infrastructure.
- Test vulnerabilities by simulating advanced persistent threats (APTs) or common attack vectors (e.g., phishing, exploitation).
- Evaluate detection and response capabilities of the
Blue Teamduring and after an attack.
How Red Teaming Supports Incident Response:
- Identifies weaknesses that could lead to security incidents.
- Improves the detection process by testing Blue Team’s ability to spot threats in real-time.
- Simulates actual cyberattacks to validate incident response plans.
2. Blue Teaming in Incident Response
The Blue Team is responsible for defending the organisation against cyberattacks, detecting intrusions, and ensuring a quick recovery from security incidents.
Goals:
- Monitor systems for suspicious activities and anomalies.
- Respond to and mitigate attacks to minimise damage and data loss.
How Blue Teaming Supports Incident Response:
- Ensures immediate containment and response during an incident.
- Protects critical assets and mitigates the effects of an ongoing attack.
- Tests response procedures through simulations and real-world attacks.
3. Purple Teaming in Incident Response
The Purple Team is a collaborative team that integrates Red and Blue Teams, enabling them to work together to enhance incident response capabilities.
Goals:
- Facilitate collaboration between Red and Blue Teams.
- Ensure that
offensive tactics(Red Team)alignwithdefensive strategies(Blue Team) to improve detection and response times.
How Purple Teaming Supports Incident Response:
- Shares knowledge between teams to identify attack patterns and improve defences.
- Helps the Blue Team better understand offensive tactics and improves their ability to detect real-world threats.
- Uses feedback loops from both Red and Blue Teams to develop more effective incident response plans.
How Red, Blue, and Purple Teams Contribute to Incident Response
| Team | Focus | Contribution to Incident Response |
|---|---|---|
| Red Team | Offensive (Simulating Attacks) | Identifies vulnerabilities and tests detection capabilities |
| Blue Team | Defensive (Responding to Attacks) | Detects, responds, and mitigates ongoing attacks, ensuring business continuity |
| Purple Team | Collaboration (Red + Blue) | Ensures Red and Blue teams work together, improving overall security posture and response strategies |
Why They Matter:
- Combining these teams enhances an organisation's ability to respond effectively to real-world cyber incidents.
- Regular simulations and collaboration ensure that both detection and response capabilities are constantly evolving.
Lab
- See the lab for IR here