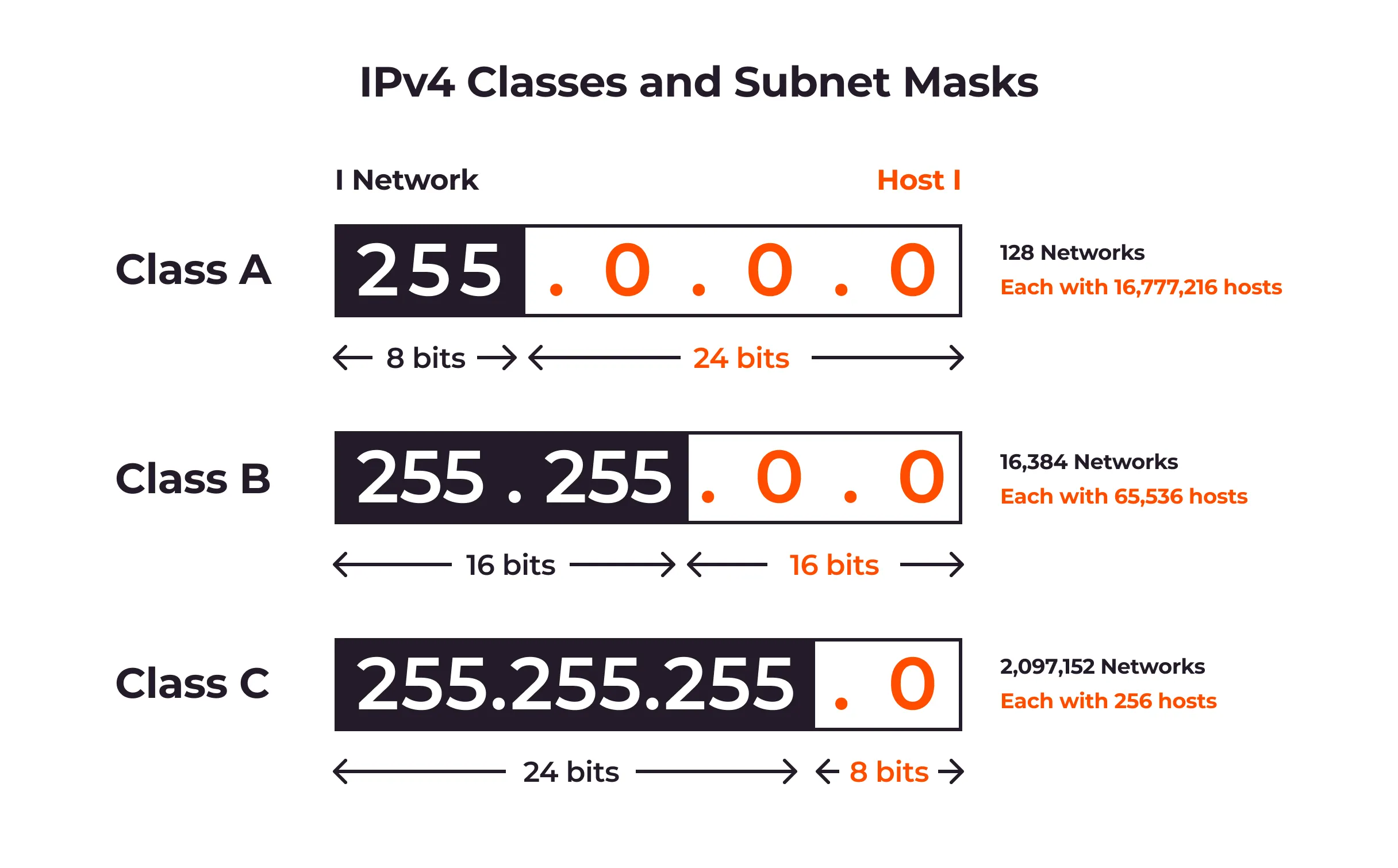
IPv4 Classes
| Class | IP Range | Start bits | Number of Networks | Number of Hosts | Total Address space |
|---|---|---|---|---|---|
| A | 0.0.0.0 - 127.255.255.255 | 0 | 128(two reserved) | 16777216 ( |
2147483648 ( |
| B | 128.0.0.0 - 191.255.255.255 | 10 | 16384 ( |
65356 ( |
1073741824 ( |
| C | 192.0.0.0 - 223.255.255.255 | 110 | 2097152 ( |
256 ( |
536870912 ( |
| D | 234.0.0.0 - 239.255.255.255 | 1110 | |||
| E | 240.0.0.0 - 247.255.255.255 | 1111 |
IPv4 Formatting
| Class | IP address Range | Formatting |
|---|---|---|
| A | 0.0.0.0 127.255.255.255 | 0NNNNNNN. HHHHHHHH.HHHHHHHH.HHHHHHHH |
| B | 128.0.0.0 191.255.255.255 | 10NNNNNN.NNNNNNNN.HHHHHHHH.HHHHHHHH |
| C | 192.0.0.0 223.255.255.255 | 110NNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH |
| D | 234.0.0.0 239.255.255.255 | MULTICASTING |
| E | 240.0.0.0 247.255.255.255 | EXPERIMENTAL |
Class D - A multicast (one-to-many) is different from a broadcast (one-to-al). Every device on a logical network must process a broadcast, whereas only devices configured to listen for a Class D address receive a multicast.
Class E - Class E addresses are reserved for experimental purposes and should not be used to address hosts or multicast groups.
Loopback Address
IP address range 127.0.0.0 to 127.255.255.255 is reserved.
This is for the loopback address network and local host.
-
Allows for a device to send and receive its own data packet
-
Allows for analysis like testing and debugging, or allowing routers to communicate in specific ways
$ cat /etc/hosts
127.0.0.1 localhost
::1 localhost
127.0.0.2 vakare
::1 vakare
IPv4 Addressing
What is this class is this address and its dotted decimal notation:
11101101.11010010.01001111.00100011
Class D237.210.79.35
10100101.00111000.00010101.10000110
Class B
165.56.21.134
00100011.10111101.00101111.10010100
Class A35.189.47.148
11000000.10101000.00000001.10001000
Class C192.168.1.136
Netmask/CIDR
-
Netmasks defines how large a network can be, this help limit the number of devices that can connect to your network. i.e., the number of the available address
-
Can help distinguish between network and host within the IP address.
-
Classless Inter-Domain Routing (CIDR)/Netmask was designed by the Internet Engineering Task Force (IETF) to slow down the exhaustion of addresses and chaotic routing tables.
-
CIDR (e.g., /32)is the number of the bit from the left
-
Size of Subnet Mask it's 32 bits
Examples
| IP Address | Netmask | Description | Netmask Length or CIDR |
|---|---|---|---|
| 192.168.55.161 | 255.255.255.255 | Only applies to 192.168.55.161 | /32 (4 octets) |
| 192.168.55.0 | 255.255.255.0 | Applies to the range 192.168.55.0-255 | /24 |
| 192.168.55.240 | 255.255.255.240 | Applies to the range 192.168.55.240-255 | /28 |
| 192.168.0.0 | 255.255.0.0 | Applies to the range 192.168.0-255.0-255 | /16 |
Netmask - Subnetting
So lets look at the binary subnet mask, we can see that /## denotes the number of ones masked off which means only the addresses not masked are available to that network.
| IP/CIDR | Binary Mask | Number of Hosts |
|---|---|---|
| 192.168.55.161/32 | 11111111.11111111.11111111.11111111 | 1 |
| 192.168.55.0/24 | 11111111.11111111.11111111.00000000 | 256 |
| 192.168.55.240/28 | 11111111.11111111.11111111.11110000 | 16 |
| 192.168.55.161/24 | 11111111.11111111.11111111.00000000 | 256 |
| 192.168.0.0/16 | 11111111.11111111.00000000.00000000 | 65536 |
| 192.168.2.1/29 | 11111111.11111111.11111111.11111000 | 8 |
Calculating the CIDR
The IP addresses range is from 21.19.35.64 and 21.19.35.127. Find the CIDR block?
CIDR block is 21.19.35.64/26
Netmask - Subnetting
So lets look at the binary subnet mask, we can see that /## denotes the number of ones masked off which means only the addresses not masked are available to that network.
11101101.11010010.01001111.00100011 /11111111.11111111.11111111.11111111
237.210.79.35/32
11000000.10101000.00000001.10001000 /11111111.11111111.11111111.00000000
192.168.1.136/24
11000000.01100101.00000101.00000000 /11111111.11111111.11100000.00000000
192.101.5.0/19
Network Address (Start Address)
-
It is the address used to identify a specific network. It represents the beginning of a range of IP addresses assigned to devices (hosts) within that network.
-
The network address is obtained by performing a logical
ANDoperation between an IP address and its corresponding subnet mask. -
This operation effectively
"masks out"the host portion of the IP address, leaving only the network portion intact -
All host bits are
0
Example
IP Address: 192.168.1.100
Subnet Mask: 255.255.255.0
-
Convert IP Address to Binary: IP=11000000.10101000.00000001.01100100
-
Convert Subnet Mask to Binary: SNM= 11111111.11111111.11111111.00000000
-
Perform Logical AND Operation:
-
Network Address: 192.168.1.0
Broadcast Address (Final Address):
The broadcast address is used to send data packets to all devices within a specific network. It represents the end of the range of IP addresses assigned to devices within that network
Example
-
Invert Subnet Mask to get Wildcard Mask: 00000000.00000000.00000000.11111111
-
Perform Logical OR Operation:
OR
=
Broadcast Address: 192.168.1.255