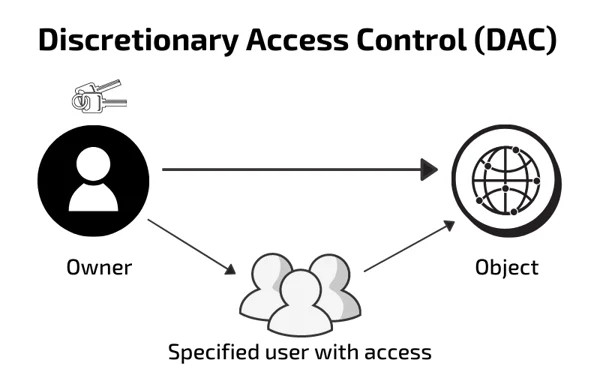
--- ### DAC's Permission Levels Permission levels indicate a subject’s rights to a system, application, network, or other resources. - **User-based**: permissions granted to a **user**. - **Job**-**based**, **group**-based, or **role**-based access control (RBAC): Permissions are based on a common set of permissions for all people in the **same** or similar **job** **roles**. - **Project-based**: Only project team has access - **Task-based**: **limits** a **person** to **executing** certain **functions** and often enforces mutual exclusivity.
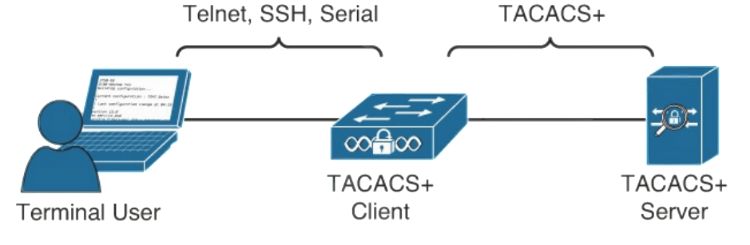 - Uses a single configuration file to: - Control server operations - Define users and attribute/value pairs - Control authentication and authorisation procedures - Allows each AAA component to be managed independently, providing greater flexibility. - Uses TCP: reliable communication.